The Platform
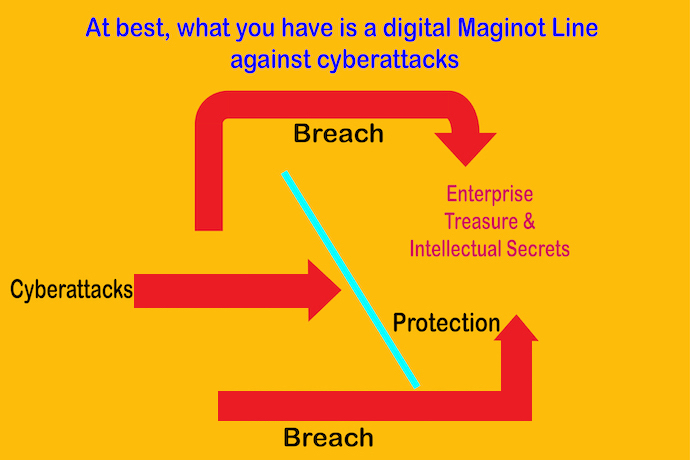
Combatting Cyberwarfare Needs Transparency
01.22.2023
James Carlini is a strategist for mission critical networks, technology, and intelligent infrastructure. Since 1986, he has been president of Carlini and Associates. Besides being an author, keynote speaker, and strategic consultant on large mission critical networks including the planning and design for the Chicago 911 center, the Chicago Mercantile Exchange trading floor networks, and the international network for GLOBEX, he has served as an adjunct faculty member at Northwestern University.