Tech
WannaCry on Cyber Monday
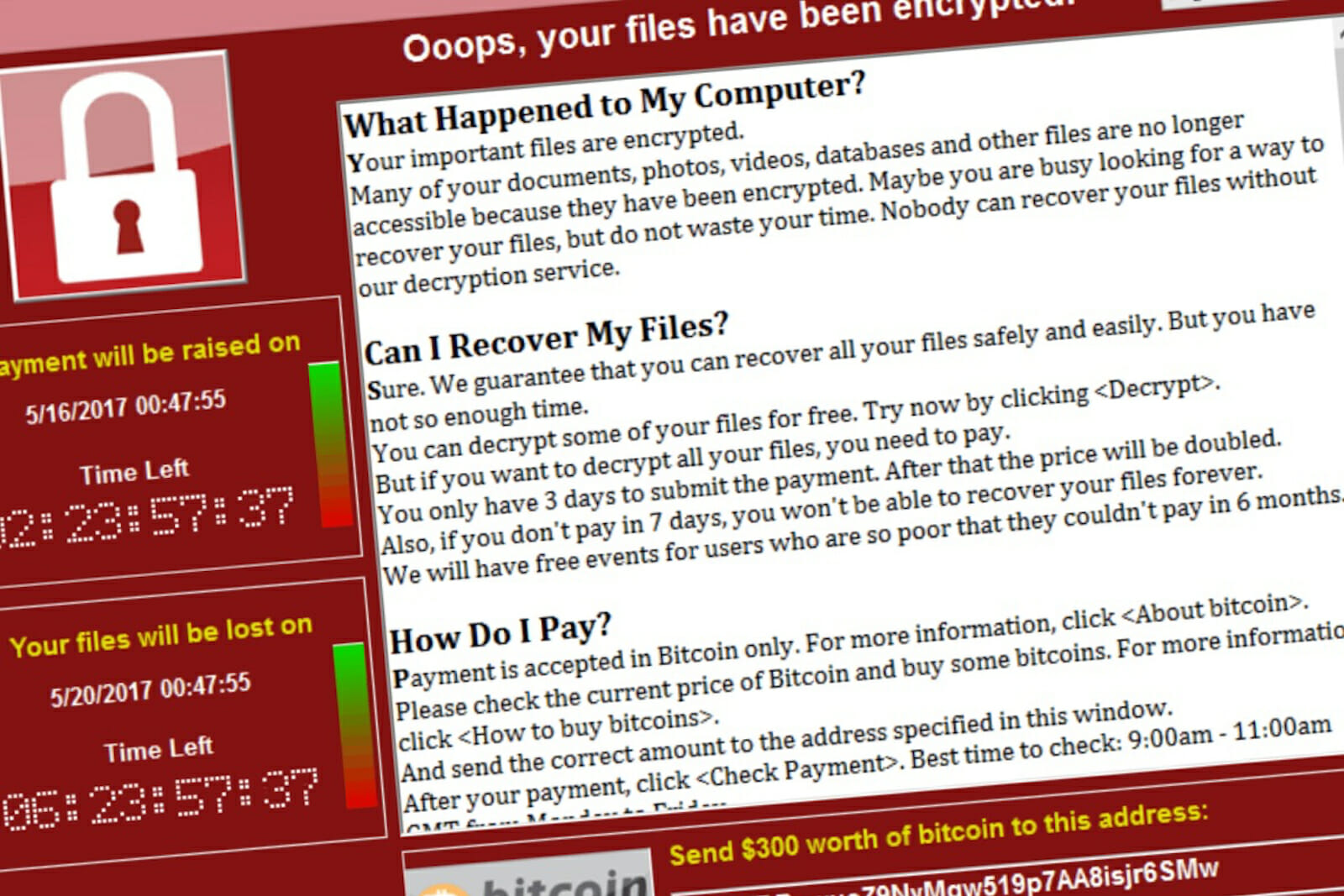
As the scale of the WannaCry cyber-attack continues to astound security experts and law-enforcement officials, we need to realize that its unprecedented spread, spanning more than 150 countries, occurred over the weekend. Within hours of its initial discovery, which was originally concentrated in Europe, the ransom attack spread to more than 70 countries within 10 hours affecting some of the largest companies around the world, such as FedEx, Spain’s Telefónica, among many other systems in both the public and private sectors. What the WannaCry exploit underscores is the speed, and geographic spread that cyber threats can have giving them a quality more akin to systemic risk than traditional siloed threats. As the work week nears and with it the opening bell for not only global trading, but also global commerce as millions of employees return to work, it is very likely we will see round two of this attack and begin to understand its true scale.
So far, a small sum of the ransom demands of $300 per locked computer have been paid. Experts estimate that no more than $30,000 in Bitcoin has been paid into accounts linked to this attack. However, with Monday nearing and with the ransom countdown clock of 3 days coming to an end, it is very likely that the attackers will get away with millions of dollars in financial demands. The true economic spoils of the largest ransomware attack thus far may only be known to the perpetrators. Worst yet, it is very likely that the spread of this attack will continue unabated as businesses turn on their lights on Monday morning. In short, the WannaCry ransomware attack underscores how cyber threats are no longer the esoteric domain for IT security professionals and government officials, but rather a top of mind business and societal concern.
While this exploit has been made possible in large part due to sensitive information that was ill-gotten from the National Security Agency (NSA), it begs the question what other payloads can be delivered through such gaping security flaws using such a powerful delivery mechanism? In this instance, the motive of the attackers is an economic one, which increases the likelihood of recovery. Indeed these types of attacks are so pernicious the FBI is giving some businesses, such as Hollywood film studios, the advice to relent and pay cyber ransoms. However, what if the attackers had a more nefarious motive than enriching themselves with Bitcoin or changing a company’s course of action? What if the payload had no discernible kill switch or readily accessible recovery method? What if the payload was delivered to critical infrastructure, such as the energy grid or financial trading platforms? In addition to concerns about what technological payloads this type of cyber atomic bomb can carry, we must also be concerned about subterfuge and the likelihood that malware is now lurking undetected in millions of computer endpoints around the world. The latency issue of cyber threats makes this risk domain one of the most complex to manage and understand.
If cyber risk came of age in 2016 with the vast array for exploits and examples of low managerial readiness. 2017 may be the year that proves the scale and consequence of this fast-moving risk. While it is not likely that the world will unplug long enough to get ahead of this risk, increasingly organizations and their leaders across all sectors need to enhance their levels of readiness. Beginning at the very top of these organizations where all too often senior leaders demonstrate tone deafness and under investment in cyber security initiatives, and ending at all organizational levels, efforts must be made to enhance both technological and human readiness to confront these threats. As the WannaCry attack will surely illustrate, all parties are effectively claiming on the scarcest of security resources – namely, the limited pool of skilled cyber security practitioners. Additionally, the information security arbitrage created by the lack of global coordination on privacy standards, will confound the search for the perpetrators.
While large enterprises, such as FedEx and Telefónica and many government agencies can marshall internal fire brigades of IT security professionals, middle-market enterprises and their smaller brethren are particularly exposed. For small to midsized enterprises cyber risks quite literally pose existential threats. Herein lies the opportunity and true purpose of the growing cyber insurance market. Part of what companies buy into with a standalone cyber insurance policy is a fire brigade that would provide remediation, public relations, and others support in these types of scenarios. Despite being the fastest growing market segment of the insurance industry, most organizations fail to appreciate cyber risk as a standalone threat. As a result, they are woefully uninsured or underinsured.
This market confusion on cyber insurance is not aided by the fact that many insurers have bundled some form of “cyber coverage” in other more mature classes of insurance. These Frankenstein products, which represent more than 95% of the cyber insurance market have produced a lot of customer confusion and the placebo effect of safety. However, all too often companies find out how little coverage they truly have during times of crisis or, given our litigious society, in courtrooms. As the WannaCry exploit reaches its peak in the coming weeks, it would be a good opportunity for organizations to revisit their posture across their technological, human and financial defenses against these types of attacks. It is very likely that these exploits will continue and as more nefarious groups learn lessons and are emboldened by the successful global deployment of the WannaCry ransomware exploit, it stands to reason that we must plan and prepare – no one more so than senior leaders and small to midsized enterprises who are in the crosshairs of increasingly complex cyber threats.

